Navigating the Wave of Fraud: A Guide to Protecting Your Restaurant’s Back Office
In the fast-paced restaurant industry, transactions are increasingly automated and the risk of fraud aimed at back-office operations is on the rise. As technology evolves, so do the tactics of cybercriminals. Safeguarding transactions and educating employees about the threat landscape is more important than ever before.
Understand The Threat of Fraud
Fraudsters are finding innovative ways to exploit vulnerabilities and compromise the financial health of restaurant and hospitality establishments. In 2023, hotels and restaurants witnessed a 14% surge in the average cost linked to data breaches. This rise in costs comes alongside the industry’s increased reliance on digital platforms and as the challenge of understaffing underscores the urgency for businesses to fortify their cybersecurity measures. Technology advancements provide necessary benefits to business owners, but they also provide cybercriminals with easier access to internal operations. If restaurants haven’t taken this into account and implemented the proper security measures, they are at a higher risk for malicious attacks.
Protecting Financial Transactions
Growing consumer awareness prompts the adoption of secure credit card transactions with encrypted data in advanced point-of-sale (POS) systems. However, the rise in digital sales at quick-service restaurants (QSR) increases the risk of credit card fraud and POS system compromises. It’s important to note that back-office operations, specifically accounts payable, are at an increased risk of being targeted by fraud due to complex supply chains and multiple vendors. Cybercriminals use tactics like phishing emails to exploit overwhelmed restaurant staff which is why vigilance and strong defenses are crucial against evolving threats to operational and financial integrity.
Fraudsters employ sophisticated tools such as chatbots and large language models to create scam emails and deceptive requests. A concerning trend involves back-office workers receiving emails that seemingly originate from familiar vendors, urging them to alter payment details for invoices. Falling victim to this scam redirects funds to criminals rather than the legitimate vendor.
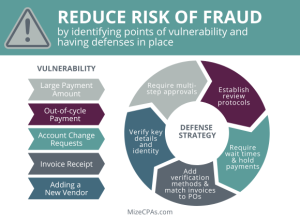
The control wielded by accounts payable (AP) departments over payments has diminished as they increasingly rely on third-party intermediaries to make payments. This expansion of the payment pathway introduces more points of vulnerability, each posing an opportunity for fraudulent activities.
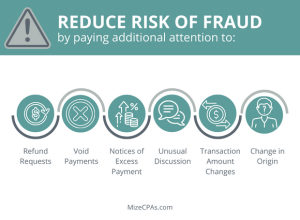
For restaurants, regardless of their format, maintaining heightened vigilance is required to detect suspicious activity or unusual requests from vendors. Onboarding new vendors amplifies risk, particularly for companies lacking policies to verify a vendor’s identity, such as conducting background checks, validating licenses, or obtaining W-9 forms and tax ID numbers. Proactive measures in these areas are essential to fortify defenses against the evolving landscape of fraudulent activities.
Businesses are increasingly establishing digital-exclusive relationships with vendors and foregoing the traditional human-to-human interactions that serves as a basic security measure. The risk of fraud further heightens when companies are making payments for intangible services, such as consulting. This is one reason it is important to seek guidance from AP experts.
Effectively defending against AP fraud involves acknowledging that cyber fraudsters have adapted to ACH payments and escalated their activities accordingly. Employees must no longer presume the legitimacy of communications, even when receiving invoices or payment requests from established vendors whose contact information appears valid. During the onboarding of new vendors, meticulous recording, and verification of crucial details, such as company/personal information and financial institution routing numbers, become essential.
In the ongoing battle against cybercrime and fraud, continual technological refinements are imperative. A robust defense hinges on educated, vigilant employees who approach security intentionally, not assuming communication is legitimate solely based on the appearance of established vendors and partners. A well-trained employee is your best defense against a potential breach that could impact the organization’s financial standing and reputation. The key to effective training lies in ensuring your employees know how to leverage technology without placing blind trust in it.